Steps Technologies IMS services help businesses manage risk and control costs by reducing total cost of ownership, speedy deployment, standardizing support processes and letting the business focus on its core competencies. These services address the requirements of organizations for effective monitoring and management of their infrastructure including servers, operating systems, networks, database, application, storage etc.
Infrastructure management services are services offered to manage essential operation components of an organization’s information technology needs. We offer a range of infrastructure management services in the following domains:
- System Management
- Network Management
- Storage Management
- Data center management
- Security management
- Desktop management
- Service desk management
The key advantages of infrastructure management are:
- Reduces duplication of efforts
- Ensure standards
- Enhances flow of information throughout an information system
- Promotes flexibility necessary for a changing environment
- Ensure easy access among organizational and external entities
Technology InfraStructure Services
Server Management

Day-to-day operational challenges and management costs of your application infrastructure are consuming a significant portion (over 70%) of your IT budget and reducing your ability to invest in programs that drive higher value for your business users.
Alert Monitoring
-
Remote monitoring of your business application on a 24x7 basis for faults, performance, and security alerts.
Resolution Management
-
Remote resolution of application infrastructure problems on a 24x7 basis for fault, performance, and security issues.
Vulnerability Management
-
Periodic and real-time scanning for vulnerabilities on your applications. Identify potential security vulnerabilities and resolve them.
User Monitoring
-
Track and report all user activity on business applications. Identify suspicious activity and take corrective action.
Backup and Archiving
-
Proactively backup the critical data stored in your business applications, and protect yourself from any critical data loss or failure of storage.
Remote AppManagement
-
Instantly solve any application issue with real-time access to Steps Technologies ’s certified database, middleware and web-service developers and managers.
Application Management

Resolution Management
-
Remote resolution of application infrastructure problems on a 24x7 basis for fault, performance, and security issues.
Vulnerability Management
-
Periodic and real-time scanning for vulnerabilities on your applications. Identify potential security vulnerabilities and resolve them.
User Monitoring
-
Track and report all user activity on business applications. Identify suspicious activity and take corrective action.
Backup and Archiving
-
Proactively backup the critical data stored in your business applications, and protect yourself from any critical data loss or failure of storage.
Remote AppManagement
-
Instantly solve any application issue with real-time access to Steps Technologies ’s certified database, middleware and web-service developers and managers.
Security Management

Protecting your corporate infrastructure and ensuring you’re your information assets are secure is no longer an afterthought; it has become the single-most business requirement on top of every CEO’s business agenda.
Steps Technologies offers proven, managed security solutions to defend against the growing threat of cyber attacks and misuse of data within the enterprise. Our managed security solutions provide end−to−end proactive and reactive security from the desktop to LAN/WAN and Internet, using a combination of innovative security methodologies and industry best practices delivered by Steps Technologies ’s experienced and certified security professionals
Intrusion Detection & Prevention
-
24x7 monitoring of your mission critical information infrastructure for any internal or external threats. This includes event correlation and analysis to eliminate false positives and proactively warn you of any threat conditions.
Perimeter Security Management
-
Remote installation, configuration and management of your perimeter security infrastructure on a 24x7 basis. Proactive identification and resolution of fault, performance, and security issues.
Vulnerability Management
-
Periodic and real-time scanning for vulnerabilities on your information infrastructure. Identify potential security vulnerabilities and resolve them.
Compliance Monitoring & Reporting
-
Track, audit and report all access to corporate information against standard compliance regulations such as SOX, PCI etc. and generate standards-compliance reporting for auditors.
Web Security Management
-
Proactively scan and detect vulnerabilities as well as offensive content on customer-facing web applications.
Network Management
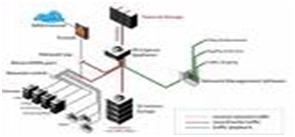
LANs WANs, VPNs, wireless networks, virtual networks and converged networks has increased management complexity. All your end-users want anytime access to their applications. New customer relationships multiply the networking technologies you need to manage. When it comes to your critical network infrastructure, the pressures you’re facing are greater today than ever before.,
Steps Technologies Network Management Service offers reliable, secure, and ITIL-compliant support and management services for any type of corporate network infrastructure.
Alert Monitoring
-
Remote monitoring of networks on a 24x7 basis for fault, performance, and security alerts. Proactively escalate issues to appropriate groups.
Vulnerability Management
-
Periodic and real-time scanning for vulnerabilities on network devices. Identify potential security vulnerabilities and resolve them.
User Monitoring
-
Track and report all user activity on critical network infrastructure. Identify suspicious activity and take corrective action.
Patch and Configuration Management
-
Proactive and timely installation critical patches and manage configurations of all your network devices. Helps prevent downtime and intrusions.
Remote NetAdmin Service
-
Instantly solve any network issue with access to real-time access to Steps Technologies ’s certified network administrators. Remote resolution for any type of network problem.
Storage Management
Our organization provides storage and backup services based on various levels of access, redundancy, performance and replication for their end-users. This is further complicated by the exponential growth of data. This demand for storage requirements combined with declining budgets requires a strategy that enables you to meet expectations without cutting corners on security and integrity of your data.
Steps Technologies ’s Storage Management Service provides a suite of services that helps you plan, implement and manage storage services without compromising security and achieving financial goals.
Storage Planning & Design
-
Understand the various user and application storage needs and develop an effective storage infrastructure design
Storage Solution Implementation
-
Install and configure storage devices, SANs, NASs and "storage clouds" that best meet the needs of your end-users and business applications.
Storage Monitoring & Management
-
Proactive monitoring of storage service levels and identify critical conditions before end-users notice performance degradation.
Storage Optimization
-
Analyze existing storage implementation, develop and implement optimization techniques to ensure best price-to-performance ratio
Backup and Archiving
-
Develop backup plans and implement backup solution to backup/archive mission-critical enterprise data for compliance and disaster-recovery scenarios.
Desktop Management

Flat or declining IT resources along with an increasingly mobile workforce is putting pressure on IT departments to continue delivering high-quality, cost-effective desktop support. In addition to this, IT is also under pressure to optimize desktop infrastructure, improve end-user productivity, secure and protect corporate desktop assets.
Steps Technologies Desktop Management Service is a fully remote-managed solution that offers world-class, reliable and secure support and maintenance services for corporate desktops.
Diagnostics and Root Cause Analysis
-
Help diagnose and identify root-cause issues for performance and security related issues with the desktop.
Security Management
-
Ensure that the desktop is free of any virus, mal-ware, ad-ware, etc. This includes a full detection and removal of security threats.
Tune-Up and Performance Management
-
Identify and resolve issues related to poor performance with the desktop. This includes disk de-fragmentation, clean up of startup files, clean cache etc.
Patch Management
-
Identify any patch anomalies with the desktop applications. and ensure that the all patch levels are current with the desktop.
Backup and Archiving
-
Proactively backup the critical data stored in your desktop, and protect yourself from any critical data loss or failure of hard disks
Remote Assist
-
Instantly solve any problem on end-user desktop using Steps Technologies ’s remote assist service. Qualified Steps Technologies experts will remotely connect to desktop and solve any desktop issue any-time anywhere.
Asset Management
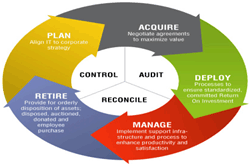
The IT Asset Management function is the primary point of accountability for the life-cycle management of information technology assets throughout the organization.
Included in this responsibility are development and maintenance of policies, standards, processes, systems and measurements that enable the organization to manage the IT Asset Portfolio with respect to risk, cost, control, IT Governance compliance and business performance objectives as established by the business.
IT Asset Management is an integrated software solution that works with all departments that are involved in the procurement, deployment, management and expense reporting of IT assets.
Business practices of STEPS Technologies:
- Uncover savings through process improvement and support for strategic decision making
- Gain control of the inventory
- Increase accountability to ensure compliance
- Enhance performance of assets and the life cycle management
- Risk reduction through standardization, proper documentation, loss detection
Process
Our business practices are process-driven and matured through iterative and focused improvements. Most successful ITAM programs are invasive to the organization, involving everyone at some level, such as end users (educating on compliance), budget managers (redeployment as a choice), IT service departments (providing information on warranties), and finance (invoice reconciliation, updates for fixed asset inventories).
IT asset management generally uses automation to manage the discovery of assets, so inventory can be compared to ownership information. Full business management of IT assets requires a repository of multiple types of information about the asset, as well as integration with other systems such as supply chain, System help desk and HR systems.
Software asset management
Software Asset Management applies to the business practices specific to software management, including software license management, configuration management, standardization of images and compliance to regulatory and legal restrictions—such as copyright law, Sarbanes Oxley and software publisher contractual compliance. Legal software use in an organization is enforced by such compliance companies as Business Software Alliance, SIIA and FAST.
Software is referred to as entitlements so that SAM programs confirm the right to use, or entitlement to that software by the user. Automation is used to facilitate this management. Microsoft maintains a list of SAM providers to help customers manage their software.
Hardware asset management
SoHardware asset management entails the management of the physical components of computers and computer networks, from acquisition through disposal. Common business practices include request and approval process, procurement management, life cycle management, redeployment and disposal management. A key component is capturing the financial information about the hardware life cycle which aids the organization in making business decisions based on meaningful and measurable financial objectives.
Service desk management

The objectives of the Service Desks are:
- Providing a single (informed) point of contact for customers
- Facilitating the restoration of normal operational service with minimal business impact on the customer within agreed SLA levels and business priorities.
The common Service Desk functions include:
- Receiving calls, first-line customer liaison
- Recording and tracking incidents and complaints
- Keeping customers informed on request status and progress
- Making an initial assessment of requests, attempting to resolve them or refer them to someone who can
- Monitoring and escalation procedures relative to the appropriate SLA
- Identifying problems
- Closing incidents and confirmation with the customers
- Coordinating second and third line support
The Service Desk pro-actively keeps users informed of all relevant service events, actions and service changes that are likely to affect them. The Service Desk is in the direct line of any impact on the Service Level Agreement (SLA) and as such should be kept rapidly informed of any planned or unexpected changes or service unavailability.






